
Fidelis Cybersecurity
Using endpoint security is more than just important. It is critical as hackers use vulnerable endpoint security as entry points to download and spread malware.
Fidelis Cybersecurity The Ultimate Endpoint Protection System for More Company's Productivity
Every company has a high risk of hacking and other threats that endanger the security of each company's network. This is how endpoint security is very important for extra protections. The security system is even needed by small companies that use internet connections for communication and advertisement media.
Fidelis Cybersecurity clear that the endpoint security system is needed for companies and also departments or organizations. But the main question is, what is actually the endpoint security and why is it really crucial? You can read the explanation below.
- Fidelis Network
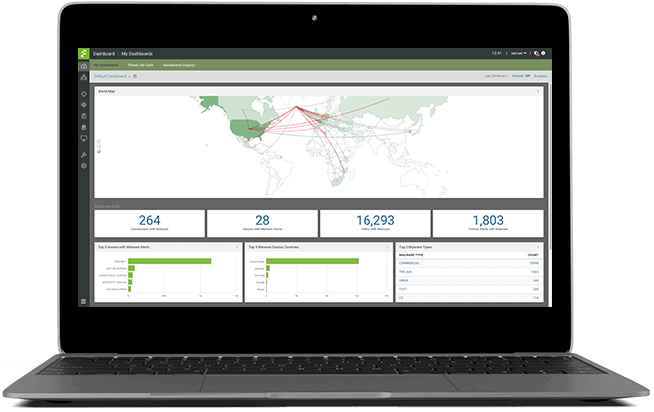
Network and Cloud Traffic Analysis across all port and protocols, Asset Classification, Treat Detection and Response, and Data Loss Prevention.
- Fidelis Endpoint
Endpoint Detection and Response that accelerates and automates investigations with deep forensics.
- Fidelis Deception
Alter your network terrain and detect post-breach attacks with automated deception layers.

Fidelis Cybersecurity Threat Detection & Response Solutions

Fidelis network
Identifying threats and data leakage requires deep inspection and analysis of all forms of content, including unpacking and extracting deeply embedded files. Fidelis Network bi-directionally scans all network traffic, regardless of port or protocol, to reveal the network and application protocols, files, and content. By conducting real-time network analysis and identifying behaviors that indicate compromises, Fidelis Network provides automated detection for the proactive discovery of attackers, suspicious hosts, and malware.
Including multiple sensors that can be placed throughout your network to enforce prevention policies. These sensors can be placed inline or out-of-band based on your network configuration and prevention tolerance. Fidelis Network detects and prevents data theft by utilizing our industry-best content decoding and inspection engine. Get ultimate visibility of exfiltration attempts and keep your sensitive data safe.

Endpoint
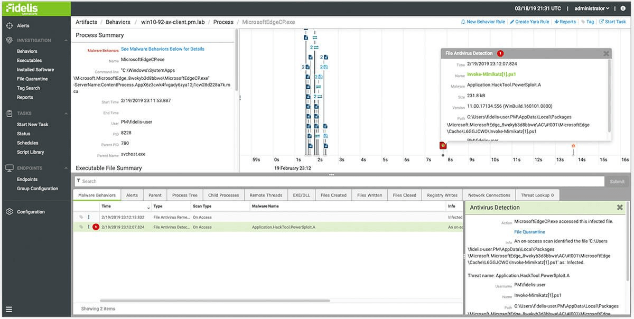
Fidelis Endpoint provides visibility into all endpoint activity including process actions, logged in users, registry writes, file system activity, and memory. Detect threats by applying Fidelis Insight threat intelligence, custom alert rules, YARA and OpenIOC formats to analyze, alert, and collect system events. Fidelis visibility is always on, whether the endpoint is on-network or off. Automatically respond to any detection by executing tasks either shipped with the system or customized for your environment. Response tasks include endpoint isolation, creating and using restore points, process termination and file wiping. You can also jumpstart investigations including memory analysis, vulnerability scans, and system inventory. Integrate with Fidelis Elevate to execute response actions to threats detected in the network.
Fidelis Endpoint can be enhanced with Fidelis AV so you can see exactly where threats originate. Fidelis AV provides both traditional signature and heuristic-based detection and prevention of threats on the endpoint. Process scanning allows users to block execution of processes by hash or with easily created YARA rules.

Deception
Classify all network assets, communication paths, and network activity to profile your users, services, and assets. The result is a network profile that includes all assets including servers, workstations, enterprise IoT devices, and shadow-IT. The profile is continuously adapted as changes occur within your environment. From automated discovery of an environment, accurate information is utilized to auto-generate decoys for deception layers. Decoys have profiles, services and activity matching the environment, plus recommended breadcrumbs for placement on nearby real assets to act as lures to decoys. Configuration options are available to customize the deception layer.
Learn what attackers do once inside your network after compromising a foothold system often from phishing or social engineering attacks. Attractive breadcrumbs placed on real assets are quickly found by attackers to lure them to decoys, interactive services and fake data. Divert attacks from real resources and data to quickly detect and defend against post-breach attacks.
Deception defenses provide a proactive opportunity to lure, detect and defend early within post-breach compromise incidents with no risk to resources or data, or impact to users and operations. Alerts come from deception layers unknown to users and partners resulting in high fidelity with no false positives. The result is a low friction, low risk accurate alarm system to detect post-breach attacks.
Ready to get started?
Call us now to get free quotation about your customize project
Call us on
