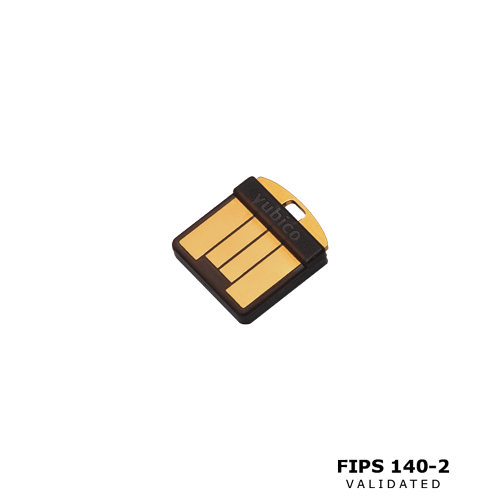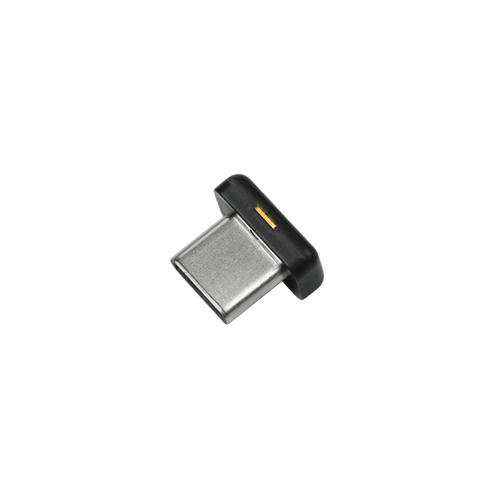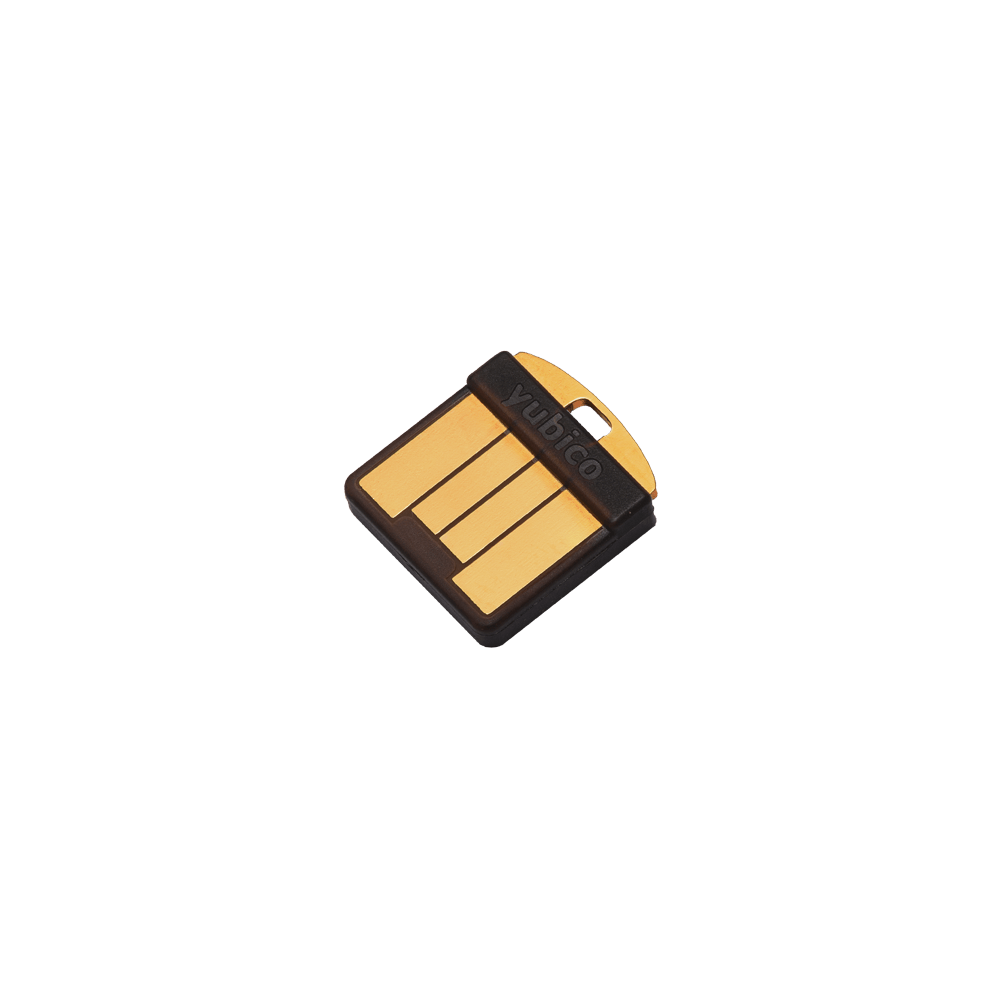
YubiHSM 2 Two Factor Authentication The Innovative Hardware Solution
The YubiHSM 2 Two Factor Authentication is the innovative hardware solution to protect your certificate authority root keys. It could be secured from any attacks such as copied by hackers, malicious insiders, and malware. This is a cheap way that you should pay. It is especially for security needs. In addition, this device has an easy deployment, that is why; it is accessible for a lot of organizations in this world. The higher level that it offers attracts so many people to try this tool.
It is reasonable since you will get better protection for the generation of a cryptographic digital key, management, and storage. Usually, this method is recommended for organizations that use the Microsoft Active Directory Certificate Services for the safety and convenience of their users.
All features owned by this YubiHSM 2 Two Factor Authentication are accessible. The most case in the industry is hardware-based digital signature verification and generation. Overall, this device has super detail and an amazing system to always protect your access.

YubiHSM 2 Two Factor Security Key The Benefits that Customer Will Get
|
You cannot deny that using this device will save more money. It is a cost-effective HSM solution in this era. In addition, the deployment is so easy. You are as a beginner can try to use this tool easily without any further issues. The secure key storage and operations are also the benefits that this Yubi will give. YubiHSM 2 Two Factor Security Key basically offering a compelling chance for securer storage, management, and generation of the keys. How the process is done? Here is the definition. YubiHSM 2 Two Factor Authentication Integrate RapidlyYubiHSM 2 Two Factor Authentication could be used as a comprehensive cryptographic toolbox, it is especially for low-volume operations so it's great to have one. Besides, it also supports PKCS#11 in the standard of the industry. Actually, this tool will make the hardware-backed keys, especially for Microsoft. Using this one will not only secure the CA root keys, but it is able to protect all verification and signing services by using private keys. It also has extensive cryptographic capabilities such as ECC, RSA, ECDSA, AES, and SHA-2. You don’t need to be worried about anything since this YubiHSM 2 Two Factor Authentication has secure key operations and storage. The session between application and HSM is also not harmful. It uses the role-based to assess controls as well for key usage and management. Furthermore, this device is equipped with 16 concurrent connections, remote management, and optionally network shareable. The good thing is that it is low-power usage and has the ‘Nano’ form factor which is so unique. It is really good. You will also love the M of N wrap key restore and backup system which is owned by this YubiHSM 2 Two Factor Authentication. It is supported by PKCS#11, interfaces through YubiHSM KSP, and native libraries. The temper evident audit logging is a pro of this tool. |
|
|
The Details of the Features YubiHSM 2 Two Factor Security KeyIt is for sure that you want to know about the feature details that it has. The first is about secure key storage and operation. Don’t worry to create, import, and also store the keys. This HSM tool will then prevent them from any theft. It will against logical attacks and also physical theft. This YubiHSM 2 Two Factor Security Key also supports the key wrapping, hashing, asymmetric signing, and also decryption operations. The next feature is a secure session between the application and this tool. It uses the modern and sophisticated protected tunnel. Furthermore, the 16 concurrent connections are also available. Most applications are able to establish sessions really well with this YubiHSM 2 Two Factor Security Key. It means that the cryptographic operations sessions will be terminated automatically. It is especially after the inactivity of long-lived. |
YubiHSM 2 Two Factor Authentication The Network Shareable FeatureThis feature is made to increase flexibility. This device is specially designed where you could manage it to be available for use over the networks of the other servers or applications, it is great for a server that hosts several virtual machines at the same time. The Remote Management feature will able to manage several deployed devices for the whole parts of the company. It means that this step can eliminate the on-call staff and also travel expenses. The Nano-form factor makes this tool can be used in the USB-A port. Make sure that your gadget or computer has this kind of port. The tamper-evident audit logging feature is also equipped. The good thing is that you could use the direct USB support feature too, it means that you can talk to the USB layer. It is able to be done without the needs of an HTTP mechanism. It is simple, but it is really improved the experience of you as the developers. It supports the virtualized environment. You can say that the YubiHSM 2 Two Factor Authentication is an all-in-one device to give so many benefits. |

Specifications of YubiHSM 2
|
|
Secure key storage and operations |
|
|
|
Extensive cryptographic capabilities: RSA, ECC, ECDSA (ed25519), SHA-2, AES |
|
|
|
Secure session between HSM and application |
|
|
|
Role-based access controls for key management and key usage |
|
|
|
16 concurrent connections |
|
|
|
Optionally network shareable |
|
|
Remote management |
|
|
|
Unique “Nano” form factor, low-power usage |
|
|
|
M of N wrap key Backup and Restore |
|
|
|
Interfaces via YubiHSM KSP, PKCS#11, and native libraries |
|
|
|
Tamper evident Audit Logging |
Are the Cryptocurrency Exchanges Safe Enough?
|
The answer is for sure yes. It cannot be denied that there are more assets that need to be protected, there is a solution to fight and secure them from any security risks. This YubiHSM 2 Two Factor Authentication is the answer. It will allow the organization to save its cryptographic key. It means that your sensitive financial information will be highly protected. Furthermore, it could save the internet of things (IoT) environment too. What is this environment means? |
|
|
Works on
More YubiKey
Ready to get started?
Call us now to get free quotation about your customize project
Call us on